CONTENTS
- OSI and TCP/IP Models
- subnetting IPv4 and IPv6
- Routing protocols
- Spanning Tree Protocol (STP) and various types
- VLAN’s and VTP
- Access Lists (AL)
- Virtual Private Network (VPN)
1) OSI model and TCP/IP model and various protocols at different layers.
OSI MODEL:
OSI standard model allows hardware to communicate through the standard communication protocol.
This model is developed by ISO in 1974, which consists of 7 layers.
a) Physical Layer
- Description: It is a lowest layer, which defines the physical characteristics of the transmission medium, including connectors, pins, use of pins, electrical currents, encoding, light modulation, and so on.
- Responsibility: Provides physical connection between devices.
- Form of Information: Bits
- Functions:
- Bit synchronization
- Bit rate control
- Physical topologies
- Transmission mode
- half duplex
- full duplex
- Devices:
- Hubs
- Repeaters
- Fibers
- Cables
- protocols:
- Ethernet
- Bluetooth
- USB
- DSL
- PON
- OTN
- IEEE 802.3, 802.11
- ISDN
b) Datalink Layer
- Description: It defines the protocols for delivering data over a particular single type of physical network (like, Ethernet data link protocol) and it addresses the way, data packets send from the one node to another.
- Responsibility: Provides node-node delivery of the message.
- Form of Information: Frames
- Functions:
- Framing
- Physical addressing
- Error control
- Flow control
- Access control
- Devices:
- 2-layer Switches
- Bridges
- NIC’s
- Modems
- DSL
- protocols:
- ARP
- CSLIP
- HDLC
- PPP
- X.25
- ATM
- SDLS
- STP
- VLAN
c) Network Layer
- Description: This layer defines the logical addressing, routing (forwarding), and the routing protocols, that are used to learn routes. It passes information between lower and higher layers, as it sits on the middle layer. It performs real time processing & transfers data from node to node.
- Responsibility: To provide addressing (IP address) & routing of packets.
- Form of Information: Packets
- Functions:
- Routing
- Logical addressing
- Devices:
- Routers
- 3-layer Switches
- Brouters
- protocols:
- IPv4
- IPv6
- IPX
- AppleTalk
- ICMP
- IPsec
- IGMP
d) Transport Layer
- Description: The layer provides backbone to the data flow between two hosts. It focuses on delivery of data between two endpoint hosts. One of the services it provides is “ERROR RECOVERY” and works on two determined communication modes.
- Responsibility:
- Transmits data from source to destination Node.
- Provides reliable and cost effective communication.
- Form of Information: Segments
- Functions:
- Segmentation & Reassembly
- Service point addressing (includes port address)
- Multiplexing
- Flow control
- Congestion avoidance
- Devices:
- Gateways and Firewalls
- Part of OS and communicate with application layer by system calls
- protocols:
- TCP
- UDP
- SCTP
- SPX
- DCCP
e) Session Layer
- Description: This layer creates a session between source and destination Nodes & terminates sessions on completion of communication process. It provides methods to group multiple bidirectional messages into a workflow for easier management and easier backout of work that happened if the entire workflow fails.
- Responsibility: Establishes and maintain connections between network applications.
- Form of Information: Session protocol data unit
- Functions:
- Session establishment, maintenance, Termination
- Synchronization
- Devices:
- Gateways and Firewalls & PC’s
- protocols:
- PPTP
- SAA
- L2TP
- NetBIOS
f) Presentation Layer
- Description: It converts data formats into a format readable by the application layer, in other words, this layer negotiates data formats, such as ASCII text, or image types like JPEG.
- Responsibility: Presents data to the application in a application understandable language.
- Form of Information: Presentation protocol data unit
- Functions:
- Translation:- ASCII to EBCDIC
- Encryption/Decryption
- Compression
- Devices:
- Gateways and Firewalls & PC’s
- protocols:
- SSL
- TLS
- XDR
- MIME
g) Application Layer
- Description: It works at the end user to interact with user applications. It provides an interface from the application to the network by supplying a protocol with the actions meaningful to the application.
- Form of Information: Application protocol data unit
- Functions:
- Network virtual terminal
- File transfer access & management
- Mail Services
- QoS
- Devices:
- Gateways and Firewalls & PCs’s
- All end devices,Phones & Servers
- protocols:
- HTTP
- SMTP
- DHCP
- FTP
- DNS
- SNMP
- Telnet
TCP/IP MODEL:
- TCP/IP set standards of how data could be transmitted between multiple networks.
- TCP/IP model is most commonly used because of its viability (ability to work successful), which supports flexible architecture and adding more machines to a network was easy. And also the network was robust & connections remained intact until the source and destination were functioning.
- It has become the base technology for global internet that connect homes.
- TCP/IP reference model consists of 4 layers
a) Network Access Layer
- Description: Network access layer is also called as Link Layer (Data Link + Physical), which refers to the physical connections or links, between two devices and the protocols used to control those links. It defines protocols and hardware required to connect a host on a physical network, in order to deliver data across it. For example, when the host’s/router’s IP process decides to send an IP packet to other host/router, It uses link-layer details to send packet to the next host/router. This layer normally consists of device drivers in the OS and the network interface card, attached to the system, where both take care of communication details with media (cable) being used to transfer the data over the network.
- Responsibility: Transfers data between devices that are on the same network.
- Functions:
- Modulation
- Line Coding
- Bit Synchronization
- Frame Synchronization
- Error Detection
- LLC & MAC sublayer functions
- protocols:
- ARP
- NDP
- IEEE 802.3, 802.11
- Ethernet
- PPP
- Frame Relay
b) Internet Layer
- Description: TCP/IP network layer includes a small number of protocols, but only one major protocol: the Internet Protocol (IP), which provides several features like, most importantly, addressing and routing. This layer helps packet to travel independently to destination. It defines protocols for logical transmission of packets over the network.
- Responsibility: It’s main purpose is to organize or handle the movement of data on network, which means
routing of the data over the network. - Functions:
- Traffic Routing
- Traffic Control
- Fragmentation
- Logical addressing
- Delivering IP packets
- Avoiding Congestion
- Performing rouiting
- protocols:
- IP
- ICMP
- IGMP
- Routing Protocols
c) Transport Layer
- Description: The layer provides backbone to the data flow between two hosts. This layer provides services to the layer higher in the TCP/IP model i.e application layer. One of the services it provides to the application layer is “ERROR RECOVERY”. It decides, whether data transmission should be done on parallel path (or) single path.
- Responsibility: It provides end-to-end transportation of data & setup’s a logical connection between hosts. (reliable transmission of data & error free delivery packets)
- Functions:
- Message segmentation
- Acknowledgement
- Traffic control
- Session multiplexing
- Error detection & correction (resends)
- Message reordering
- protocols:
- TCP
- UDP
- Provides flow control
- Connection establishment
- Reliable data delivery
- Provides a basic datagram service with no reliability guarantees
- SPX
d) Application Layer
- Description: It defines protocols for node-to-node application communication and provide service to the application software running on a computer. Application layer does not define the application itself, but it defines services that applications need. It provides services to the application software running on a computer. In other words, the application layer provides an interface between software running on a computer and the network itself.
- Responsibility: It is responsible for handling all process-process communication functions.
- Functions:
- Session establishment
- Maintenance
- Termination
- Character code translations
- Data conversions
- Compression’s
- Encryption
- Remote access
- Nkt management
- protocols:
- Pipes
- NetBIOS
- MIME
- TLS
- SSL
- FTP
- DNS
- HTTP
- SMTP
- Increase routing efficiency
- Enhancing security of network
- Reducing size of broadcast domain
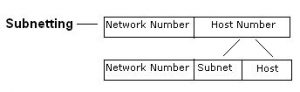
- For subnetting a network, we add more bits from the host portion to the subnet mask. Subnet mask is a 32 bit number that masks an IP address which divides IP address into Network address & host address.
- Systems with same subnet can communicate directly with each other , while systems on different subnets communicate through a Router.
Class Denotion Prefix bits (leading bit pattern) Decimal range Max networks Max nodes per network A net.node.node.node 0 1 – 127 127 16,777,214 B net.net.node.node 1 0 128 – 191 16,384 65,534 C net.net.net.node 1 1 0 192 – 223 2,097,152 254 D 1 1 1 0 E 1 1 1 1 - If number of networks increases, the number of nodes decreases
Example: Class 'C' addressing 255.255.255.0 (default (class C) mask) -> denoted as /24 (based on CIDR) /24 => 11111111. 11111111. 11111111. 00000000 -> 255.255.255.0 ↱Stolen bit from host bits /25 => 11111111. 11111111. 11111111. 10000000 -> 255.255.255.128Length of subnet mask bits Default subnet mask subnets Hosts /24 255.255.255.0 28 – 2 = 254 /25 255.255.255.128 0 27 – 2 = 126 /26 255.255.255.192 2 26 – 2 = 62 /28 255.255.255.240 14 24 – 2 = 14 -
For given IP address 10.1.1.1/16 => 16 bits are used for net mask => 255.255.0.0 (subnet mask) -
Number of address present in a subnet of prefix length (/29) is IPv4 -> 2(address length - prefix length) = 232-29 = 8 addresses For (/55) of IPv6 -> 2(address length - prefix length) = 2128-55 = 273 addresses - /prefix length is given in CDIR notation (Classless Inter Domain Routing), In order to improve space
utilization & routing scalability in the internet.
2) Subnetting IPv4 and IPv6
Subnetting is dividing a network into two or more smaller networks. It helps to:
Subnetting IPv4
Example: Subnet mask -> 255.255.255.192 → 11000000➔ 22-2=2 subnets & 26-2=62 hosts
Without subnetting -> 192.9.200.01000000 -> Host range address from [65 - 126]
With subnetting -> 192.9.200.10000000 -> Host range address from [129 - 190]
Subnetting IPv6
- Represented by 128 - bit addressing format
- Uses 16 byte hexadecimal number and field separated by colon (:).
________ : _______ : _______ : _______ : _______ : _______ : _______ : _______ 16 byte 16 16 16 16 16 16 16 16 x 8 = 128 bit- 16 byte = 4 hexdecimal digits (0000 - FFFF)
- 0 47 48 63 64 128
Network address range Subnetting Range Device (Interface Range) - Default is /48 -> which implies no subnetting.
3) Routing protocols
- The main purpose of routing protocol is to maintain routing tables that are used between routers.
- These protocols only share routing information between routers and don?t send end user data from network to network.
- It is also called as routing policy.
- Routing protocols are configured on routers with the purpose of exchanging routing information.
Interior Gateway Protocols Exterior Gateway Protocols Link State Distance Vector - OSPF
- IS-IS
- RIP
- IGRP
- BGP
- EGP
- Network communication occurs within small logical groups of nodes such as Domains/ Autonomous Systems (AS) / areas. The routing within an area / domain is called intra-domain routing.
Interior Routing Protocol:
It is implemented at internet layer of the TCP/IP protocol suite. To accomplish routing an interior router can use IP routing protocol and a specific routing algorithm.
a)Link State:
- It is also called shortest path first which understands whole network better than distance vector and never listens to second-hand information.
- This routing algorithm maintains more complex table of topology information. The listed best paths are not only simple but also efficient.
- Once tasks are completed the router can use table for switching packet traffic.
- Link-state understands it’s most efficient path because it doesn’t simply base it’s path decisions on hop count, it also analyzes bandwidth availability and amount of congestion on links to state which is the best path
- It is widely used and supported routing protocol. It is a open standard RP, where mostly any router support it.
- It is based on Link state algorithms and is deployed on Autonomous Systems (AS) where a group of routers share a routing protocol.
- It’s features are:
- Support for one or more metrics
- Type of service routing (TOS)
- Variable-length subnet masks (VLSMs) -> Falls into classless category
- The main purpose of this routing protocol is to learn routes. It does this by learning about every router and subnet within the whole network, resulting every router has the same information about the network same as others.
- The routers learn information by sending out LSA’s (Link State Advertisement). These LSA contains information about the subnet, router and some of the network information.
- Once LSA’s are flooded, the OSPF keeps the all of this information in a LSDB (Link State DataBase).
- The main goal of OSPF is to have same information in the LSDB’s.
- This process is obtained by three main steps:
- Become Neighbors
- Exchange database information
- Choose the best route ( by running the calculation SPF)
- Metric of OSPF is 108/Bandwidth = Cost
- OSPF has scalability issue in order to connect with larger networks. Even if we use virtual link to connect networks, it creates the copy of LSA’s which get overloaded (should not be practiced for larger networks).
- This routing protocol is similar to OSPF that have same features as both are Link state protocols, which are going to maintain link state information of the every router.
- IS-IS is protocol Independent i.e supports TCP/IP, IPX, AppleTalk.
- IS-IS communication is nothing but router-to-router information. It is originally designed as dynamic routing protocol for Connectionless Network Protocol (CLNP) which is a OSI layer protocol.
- It is later developed to support TCP/IP called as Dual IS-IS. It functions in a similar way as OSPF but
with fast convergence and more stable protocol compared to OSPF and make efficiently use of bandwidth, memory & CPU resources. - Default metric is 10 (though the interface is fast/slow).
- It understands the direction and distance of any network connection on the internetwork. It listens to second hand information to get its updates.
- The routers discover best paths to the destination networks based on the number of hops the routers are from each neighbor.
- It is a distance vector routing protocol which employ the hop count as a routing metric and it prevents routing loops by implementing a limit on the number of hops allowed in a path from source to destination.
- It is used for small organizations and is generally a classful routing protocol.
- In 1990’s RIPv2 has many enhancements that v1, instead of using broadcasts to speak with other routers, it uses Multicast address to send advertisements, specifically (224.0.0.9).
- It even supports VLSM (Classless addressing) and also IPv4 (same as RIPv1) but unable to support IPv6.
- Whereas RIPng (next generation) supports IPv6 addressing and Multicasts address of (FF02::9) and also supports VLSM and it is designed for IPv6.
- RIP implements the split horizon, route poisoning and hold down mechanisms to prevent incorrect routing information from being propagated.
- RIP protocol cannot handle big networks because it has very less hop counts ~16.
- It is a Interior gateway protocol, designed to be used within a single Autonomous System (AS).
- It is an advanced distance vector protocol, that works slightly differently than RIP and also includes some link state features.
- The main purpose of EIGRP is to learn the best route of any given subnet within a network.
- It does in a three step process:
- Becoming Neighbors
- Exchange routing information – exchange their topology information
- Choose the best routes
- While two routers are communicating, they must have same autonomous system number (AS number) that is set by configuring EIGRP on the router and must belong to same subnet.
- EIGRP doesn’t use TCP/UDP to sent update type message instead it use Reliable Transport Protocol (RTP). Because RTP use the sequence numbers to identify if messages have reached the neighbors.
- Metric calculation = ((107/least Bandwidth) + cummulative delay) x 256
- There are only applied to Cisco routing protocols and have hop count of 100.
-
Broder Gateway Protocol:<
- BGP is an inter- autonomous system protocol. It can determine routing loops.
- For communicating with two BGP neighbors, they must be on the same physical network.
- BGP metric is defined by the degree of preference for a particular path. The preference is based on Autonomous system count and the type of link etc.
- BGP keep’s track of all possible routes to destination, but advertises only if it considered to be the
best route. The update msg’s contain both network number and an autonomous system path. - As BGP lists route to destination, it prevents counting to infinity (routing loop) and slow convergence problems.
- Different types of STP:
- STP/ 802.1D – original STP – slow convergence
- PVST+ – Cisco improvement of STP adding a per VLAN feature – slow convergence
- RSTP/ 802.1w – Improved STP with much faster convergence – Fast convergence
- Rapid PVST+ – Cisco improvement of RSTP adding per VLAN feature – Fast convergence
- All above stated types of STP use a very similar method.
- It’s feature used to prevent loops when using redundant switches ( facing problems like duplicate frames, Broadcast storm, unstable MAC address table (they update repeatedly).
- Solution is, the switches simply block the ports.
- To achieve this, STP follows a strict process to decide which port to block:
- Elect a root bridge
- Place root interfaces into a Forwarding State
- Each non-root switch selects its root Port
- Remaining links choose a Designated port
- All other ports are put into a blocking state
- Root Ports: the best port to reach the Root Bridge
- Designated Port: Port with one best route to the root bridge on a link
- Non-designated Port: All other ports are in a blocking state
- Forwarding: Sending and receiving traffic like normal
- Blocking: A port that is blocking traffic
- Listening: Not forwarding traffic and not learning MAC addresses (15 seconds)
- Learning: Not forwarding traffic but learning MAC addresses (15 seconds)
- Disabled: A port that is shutdown
- Virtual Local Area Networks (VLANs) separate an existing physical network into multiple logical networks.
- Generally defined as group of devices on one or more LAN’s, that are configured to communicate as if they are on the same wire.
- They are based on logical instead of physical connections and are flexible.
- VLAN’s define broadcast domain in layer 2 network, which is a set of all devices that will receive broadcast frames originating from any device within set.
- Layer 2 switches create broadcast domains based on the configuration of the switch. Switches are multiport bridges that allow you to create multiple broadcast domains.
- Each broadcast domain is like a distinct virtual bridge within a switch.
- We can define one or many virtual bridges within a switch. Each virtual bridge you create in the switch defines a new broadcast domain (VLAN).
- To interconnect two different VLANs, you must use routers or Layer 3 switches.
- Main advantage of using VLAN is:
- It address issues such as scalability, security, and network management
- Network architects set up VLANs to provide network segmentation
- Routers between VLANs filter broadcast traffic, enhance network security, perform address summarization, and mitigate network congestion.
- It is VLAN Trunking Protocol, which is Cisco proprietary protocol used by Cisco switches to exchange VLAN information.
- VTP helps to synchronize VLAN information (VLAN ID/ VLAN name) with switches within same VTP domain
- The VTP Modes are:
- Server mode(default)
- Can create VLAN’s and sends updates & advertises VTP databases
- Servers other switches
- Client mode
- Cannot create VLAN’s
- Can sends updates & advertises VTP databases
- Transparent mode: (almost VTP disabled)
- Can create local VLAN’s
- Do not create or send database updates
- Does forward other switch advertisements
- Server mode(default)
- In order to make VTP work, the requirements are:
- All links must be trunks. No VTP msg will be send through access ports.
- All switches must have same VTP domain name.
- All switches must have Same VTP password (if enabled/set)
- ACL are essential lists of conditions that control access.
- Access list filter unwanted packets and be used to implement security policies and reducing network attacks.
- These are powerful tools that control access for packets being forwarded or blocked at the router’s interface based on the criteria specified within the access lists.
- Once the lists are built, they can be applied to either inbound or outbound traffic on any interface.
- To make use of ACLs, The system administrator must first configure ACLs and then apply them to specific interfaces.
- Applying access lists will then cause the router to analyze every packet crossing that interface in the specified direction and take action accordingly.
- When applying ACL to individual interfaces, only one access list per protocol is allowed inbound and that only one access list per protocol is allowed outbound.
-
- Standard IPv4 ACLs allows filtering based on source address
- Extended IPv4 ACLs allows filtering based on source and destination address as well as protocol
and port number.
- Standard and extended Cisco IOS access control lists (ACL) are used to classify IP packets.
- For example: If you want to allow entire network access – not one part of it (or) want to allow one part but deny access of the rest nodes, we make use of Wildcard Masking.
- It allows to create secure connection to another network over the internet. The encrypted connection ensure that sensitive data is safely transmitted.
- VPN is used to access region-restricted websites, shielding the browser activity from eavesdropping on the traffic and allows user to work remotely.
- The encryption and anonymity that a VPN provides protects all of your online activities like sending emails, shopping online, or paying bills. VPNs also help keep your Web browsing activity to be anonymous.
- The VPN create data tunnel between local network and an exit node in another location, which could be some miles away, making it seem like you are at different location.
- It works:
- By creating a point-to-point connection that cannot be accessed by unauthorized access
- To create VPN tunnel the end point devices needs to be running a VPN client (software application) locally. VPN client runs in the background and is not noticeable to other user.
- Protocols used in VPN are:
- IP security (IPsec)
- Secure Sockets layer (SSL) and transport layer Security (TLS)
- Point-to-Point Tunneling Protocol (PPTP)
- Layer-2 tunneling protocol (L2TP)
- Different types of VPNs are:
- Remote access VPN – relies on either IPsec or SSL to secure connection
- Site-to site VPN – use IPsec
- Mobile VPN
- Hardware VPN
- VPN appliance – uses SSL
- VPN Reconnect
- Dynamic multipoint virtual private network (DMVPN)
1) OSPF (Open Shortest Path First):
2) IS-IS (Intermediate System):
b) Distance Vector
1) RIP( Routing Information Protocol):
oldest protocol
2) EIGRP (Enhanced Interior Gateway Routing Protocol):
[world of Cisco]
Exterior Routing Protocol:
They are designed to communicate between autonomous systems (AS). They are complex, because they need to have more information about more number of routers.
4) STP (Spanning Tree Protocol) and various types:
| Roles | States |
|---|---|
|
|
|
5) VLAN’s and VTP:
VLANS’s (Virtual Local Area Network):
VTP:
6) Access Lists:
7) VPN (Virtual Private Network):
